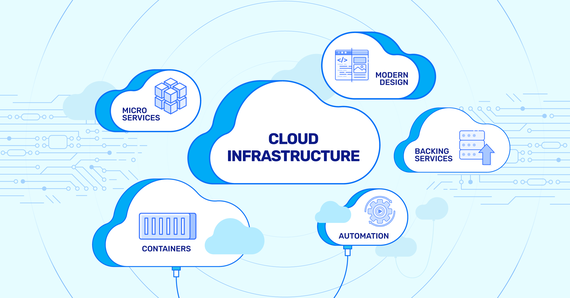
Why Cloud-Native Transformation Should Be a Part of Your Digital Strategy
Digital transformation has reshaped how businesses operate, keeping customers at the forefront. Its urgency …
A software supply chain comprises the code, people, system, and processes of creating, distributing, and maintaining software. In short, anything that touches it at any point. Software supply chain attacks are not new but have recently become more dangerous. Exposed to weak links across the software development life cycle, a vulnerability at any stage or in any dependencies can make your software susceptible to a potential compromise.
According to a report by Gartner, by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains. Overcoming this issue requires companies to develop a robust plan to keep their software safe throughout its creation and distribution.
Therefore, Software supply chain security refers to the set of practices and measures that an organization must implement to safeguard their software from potential threats and supply chain vulnerabilities. These measures include conducting code reviews, managing dependencies, verifying software authenticity, and monitoring continuously to ensure software integrity.
Companies must adopt a couple of secure methods: Code & Artifacts Signing.
Code signing is a security practice that utilizes a unique digital signature to sign software code. The signature is a marker of authenticity, verifying that the code has not been tampered with or altered. The transparency provided by code signing enables tracking and helps pinpoint the root cause of security issues or breaches in the software supply chain.
Companies not opting for code signing can face a range of issues:
When code signing and artifacts signing practices are implemented, tools like gitSign, GPG/PGP, CoSign, in-toto would make your life easy to sign every git commit and also artifacts like container images. Since signing git commits is very simple, we will skip explaining it here. If you want to learn step-by-step about gitsign and cosign, you can refer here.
The OIDC (OpenID Connect) approach is a secure authentication and authorization protocol used to verify the identity of users in web applications and APIs. It combines the capabilities of OAuth 2.0 with identity verification, enhancing security by confirming the authenticity of users before granting access to resources.
Compage leverages the capabilities of Sigstore and its integration with the Cosign tool. Sigstore, an open-source tool, enhances software supply chain security by providing transparency and verification for software artifacts. It accomplishes this through the Cosign tool, which is used for signing Docker images.
Signing Docker images with Sigstore involves a keyless approach, where the Social Login mechanism (login via GitHub, Google, Microsoft, etc.) serves as the authentication provider, guaranteeing user authentication and identity verification with Human interaction.
When someone attempts to access these signed Docker images, a dual-check approach comes into play. This dual-check approach ensures that only authenticated users can sign or access images, making it difficult for unauthorized parties to tamper with the images.
Integrating Compage with signing container images capability is a proactive step in mitigating risks associated with compromised images and their artifacts. Now, as supply chain attacks are a growing concern, our framework acts as a safeguard, helping prevent unauthorized changes to software components and artifacts, thus maintaining the reliability of the software supply chain for the code generated via Compage.
Want to see Compage in action? Check it out on GitHub. You can also get started by checking out Compage documentation for more details. If you like what we are doing, please leave us a star. And, if there are any burning questions we have not yet answered, feel free to contact us via LinkedIn. We would love to talk to you!

Digital transformation has reshaped how businesses operate, keeping customers at the forefront. Its urgency …

Gone are the days of monolithic applications and siloed data centres. Enterprises are increasingly adopting …
Gone are the days of simple, monolithic applications running on a centralized infrastructure. Today’s …
Finding the right talent is pain. More so, keeping up with concepts, culture, technology and tools. We all have been there. Our AI-based automated solutions helps eliminate these issues, making your teams lives easy.
Contact Us